mirror of
https://github.com/elastic/kibana.git
synced 2025-06-28 03:01:21 -04:00
## Summary Adds an API route for `execute` endpoint response action. **RBAC control** 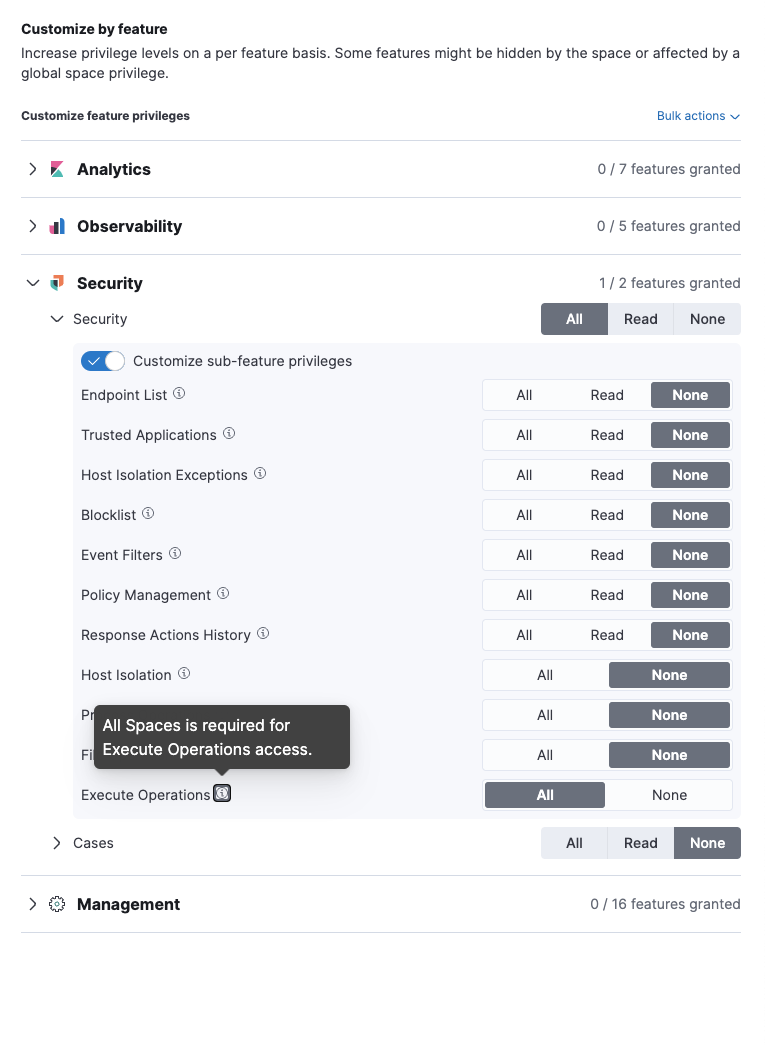 **successful req/res**  <details> <summary>**.logs-endpoint.actions-default doc source**</summary> ```json5 { "EndpointActions": { "data": { "comment": " get list of files", "parameters": { "command": "ls -al", "timeout": 2500 }, "command": "execute" }, "action_id": "dae148b2-aaaf-4a7e-b5e3-0c530dafc974", "input_type": "endpoint", "expiration": "2023-02-10T15:54:45.768Z", "type": "INPUT_ACTION" }, "agent": { "id": [ "cef48f14-d4ae-4bd6-a281-d5aba6b9c88a" ] }, "@timestamp": "2023-01-27T15:54:45.768Z", "event": { "agent_id_status": "auth_metadata_missing", "ingested": "2023-01-27T15:54:45Z" }, "user": { "id": "elastic" } } ``` </details> <details> <summary>*.fleet-actions doc source*</summary> ```json5 { "action_id": "dae148b2-aaaf-4a7e-b5e3-0c530dafc974", "expiration": "2023-02-10T15:54:45.768Z", "type": "INPUT_ACTION", "input_type": "endpoint", "data": { "command": "execute", "comment": " get list of files", "parameters": { "command": "ls -al", "timeout": 2500 } }, "@timestamp": "2023-01-27T15:54:45.768Z", "agents": [ "cef48f14-d4ae-4bd6-a281-d5aba6b9c88a" ], "timeout": 300, "user_id": "elastic" } ``` </details> ### Checklist - [x] [Unit or functional tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html) were updated or added to match the most common scenarios ### For maintainers - [ ] This was checked for breaking API changes and was [labeled appropriately](https://www.elastic.co/guide/en/kibana/master/contributing.html#kibana-release-notes-process)
209 lines
9.1 KiB
TypeScript
209 lines
9.1 KiB
TypeScript
/*
|
|
* Copyright Elasticsearch B.V. and/or licensed to Elasticsearch B.V. under one
|
|
* or more contributor license agreements. Licensed under the Elastic License
|
|
* 2.0; you may not use this file except in compliance with the Elastic License
|
|
* 2.0.
|
|
*/
|
|
|
|
import util from 'util';
|
|
import { isEqual, isEqualWith } from 'lodash';
|
|
import { FtrProviderContext } from '../../ftr_provider_context';
|
|
|
|
export default function ({ getService }: FtrProviderContext) {
|
|
const supertest = getService('supertest');
|
|
|
|
describe('Privileges', () => {
|
|
describe('GET /api/security/privileges', () => {
|
|
it('should return a privilege map with all known privileges, without actions', async () => {
|
|
// If you're adding a privilege to the following, that's great!
|
|
// If you're removing a privilege, this breaks backwards compatibility
|
|
// Roles are associated with these privileges, and we shouldn't be removing them in a minor version.
|
|
const expected = {
|
|
features: {
|
|
discover: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
visualize: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
dashboard: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
dev_tools: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
advancedSettings: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
indexPatterns: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
savedObjectsManagement: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
savedObjectsTagging: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
graph: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
maps: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
generalCases: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
observabilityCases: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
canvas: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
infrastructure: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
logs: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
uptime: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
apm: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
osquery: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
ml: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
siem: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
securitySolutionCases: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
fleetv2: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
fleet: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
stackAlerts: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
actions: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
filesManagement: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
filesSharedImage: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
rulesSettings: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
},
|
|
global: ['all', 'read'],
|
|
space: ['all', 'read'],
|
|
reserved: ['fleet-setup', 'ml_user', 'ml_admin', 'ml_apm_user', 'monitoring'],
|
|
};
|
|
|
|
await supertest
|
|
.get('/api/security/privileges')
|
|
.set('kbn-xsrf', 'xxx')
|
|
.send()
|
|
.expect(200)
|
|
.expect((res: any) => {
|
|
// when comparing privileges, the order of the privileges doesn't matter.
|
|
// supertest uses assert.deepStrictEqual.
|
|
// expect.js doesn't help us here.
|
|
// and lodash's isEqual doesn't know how to compare Sets.
|
|
const success = isEqualWith(res.body, expected, (value, other, key) => {
|
|
if (Array.isArray(value) && Array.isArray(other)) {
|
|
return isEqual(value.sort(), other.sort());
|
|
}
|
|
|
|
// Lodash types aren't correct, `undefined` should be supported as a return value here and it
|
|
// has special meaning.
|
|
return undefined as any;
|
|
});
|
|
|
|
if (!success) {
|
|
throw new Error(
|
|
`Expected ${util.inspect(res.body)} to equal ${util.inspect(expected)}`
|
|
);
|
|
}
|
|
})
|
|
.expect(200);
|
|
});
|
|
|
|
it('should include sub-feature privileges when respectlicenseLevel is false', async () => {
|
|
const expected = {
|
|
global: ['all', 'read'],
|
|
space: ['all', 'read'],
|
|
features: {
|
|
graph: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
savedObjectsTagging: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
canvas: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
maps: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
generalCases: ['all', 'read', 'minimal_all', 'minimal_read', 'cases_delete'],
|
|
observabilityCases: ['all', 'read', 'minimal_all', 'minimal_read', 'cases_delete'],
|
|
fleetv2: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
fleet: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
actions: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
stackAlerts: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
ml: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
siem: [
|
|
'actions_log_management_all',
|
|
'actions_log_management_read',
|
|
'all',
|
|
'blocklist_all',
|
|
'blocklist_read',
|
|
'endpoint_list_all',
|
|
'endpoint_list_read',
|
|
'event_filters_all',
|
|
'event_filters_read',
|
|
'host_isolation_all',
|
|
'host_isolation_exceptions_all',
|
|
'host_isolation_exceptions_read',
|
|
'minimal_all',
|
|
'minimal_read',
|
|
'policy_management_all',
|
|
'policy_management_read',
|
|
'process_operations_all',
|
|
'read',
|
|
'trusted_applications_all',
|
|
'trusted_applications_read',
|
|
'file_operations_all',
|
|
'execute_operations_all',
|
|
],
|
|
uptime: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
securitySolutionCases: ['all', 'read', 'minimal_all', 'minimal_read', 'cases_delete'],
|
|
infrastructure: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
logs: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
apm: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
discover: [
|
|
'all',
|
|
'read',
|
|
'minimal_all',
|
|
'minimal_read',
|
|
'url_create',
|
|
'store_search_session',
|
|
],
|
|
visualize: ['all', 'read', 'minimal_all', 'minimal_read', 'url_create'],
|
|
dashboard: [
|
|
'all',
|
|
'read',
|
|
'minimal_all',
|
|
'minimal_read',
|
|
'url_create',
|
|
'store_search_session',
|
|
],
|
|
dev_tools: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
advancedSettings: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
indexPatterns: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
filesManagement: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
filesSharedImage: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
savedObjectsManagement: ['all', 'read', 'minimal_all', 'minimal_read'],
|
|
osquery: [
|
|
'all',
|
|
'read',
|
|
'minimal_all',
|
|
'minimal_read',
|
|
'live_queries_all',
|
|
'live_queries_read',
|
|
'run_saved_queries',
|
|
'saved_queries_all',
|
|
'saved_queries_read',
|
|
'packs_all',
|
|
'packs_read',
|
|
],
|
|
rulesSettings: [
|
|
'all',
|
|
'read',
|
|
'minimal_all',
|
|
'minimal_read',
|
|
'allFlappingSettings',
|
|
'readFlappingSettings',
|
|
],
|
|
},
|
|
reserved: ['fleet-setup', 'ml_user', 'ml_admin', 'ml_apm_user', 'monitoring'],
|
|
};
|
|
|
|
await supertest
|
|
.get('/api/security/privileges?respectLicenseLevel=false')
|
|
.set('kbn-xsrf', 'xxx')
|
|
.send()
|
|
.expect(200)
|
|
.expect((res: any) => {
|
|
// when comparing privileges, the order of the privileges doesn't matter.
|
|
// supertest uses assert.deepStrictEqual.
|
|
// expect.js doesn't help us here.
|
|
// and lodash's isEqual doesn't know how to compare Sets.
|
|
const success = isEqualWith(res.body, expected, (value, other, key) => {
|
|
if (Array.isArray(value) && Array.isArray(other)) {
|
|
return isEqual(value.sort(), other.sort());
|
|
}
|
|
|
|
// Lodash types aren't correct, `undefined` should be supported as a return value here and it
|
|
// has special meaning.
|
|
return undefined as any;
|
|
});
|
|
|
|
if (!success) {
|
|
throw new Error(
|
|
`Expected ${util.inspect(res.body)} to equal ${util.inspect(expected)}`
|
|
);
|
|
}
|
|
})
|
|
.expect(200);
|
|
});
|
|
});
|
|
});
|
|
}
|